

College Day RSA Conference
DON’T MISS OUT ON RSAC COLLEGE DAY College students and recent grads are invited to one FREE day of Full Conference access on April 19 ...

FruitFly Malware
A Justice Department indictment alleges a 28-year-old hacker from Ohio, created the FruitFly malware and spied on Apple computers for 13...
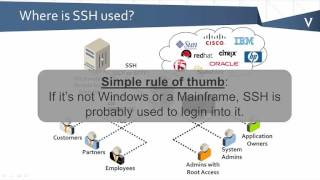

SSH Encryption Analysis
Eric Ilmberger CNT52 Network Fundamentals I did a little more research on symmetrical and asymmetrical encryption because it wasn't...


AI in Hacking
Eric Ilmberger CNT 52 Network+ I went looking for news on mass AI attacks but was unable to really find anything. As AI develops further...


12 DEC 2017 Security Update
In this issue will will cover recent news topics in cyber security. #Security #Antimalware #Malware #Hacker #Hacking #Cybercrime...


Hacking Cars, Plans, and Devices
How safe are we? If planes can be hacked and cars can be hacked, what is preventing terrorists or contract killers from hacking vehicles...


Cyber-espionage Technology Ups the Game
Espionage is nothing new, with the advent of technology why wouldn’t spies take full advantage of the benefits and ease of use technology...


Chaos to Control
From the way-back machine. Almost two decades ago, when I did IT services for clients, I came up with this as an information sheet for...


Hacking the iPhone's Face ID
A Vietnamese security firm says it has been able to fool the iPhone X's facial recognition software. In a video released by the company...

Where Cybercrime Goes to Hide
Here is a Norton documentary on bulletproof hosting services. Pick where you want to host your data where it is most legally beneficial...














