

The Wolf
Stop what you are doing and watch this. It's a big ad for HP but you gotta take a minute to view it. Especially after what we were...


Hackers Steal Celebrity Plastic Surgery Photos
Hackers Steal Celebrity Plastic Surgery Photos, Demand Ransom (The Young Turks) Hackers are demanding big money to not release plastic...
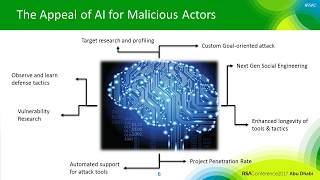

AI in Cyber-security
Here are some views on how AI can help cyber-security efforts. My opinion is we need to adopt AI for cyber-security before hackers learn...


Ted Talk - Cybercrime
James Lyne: Everyday cybercrime -- and what you can do about it "How do you pick up a malicious online virus, the kind of malware that...


New Attack Techniques 2017
The Seven Most Dangerous New Attack Techniques, and What's Coming Next "Moderator: Alan Paller, Research Director and Founder, SANS...
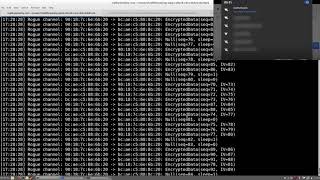

WPA2 Vulnerability
WPA2 Encryption used to secure wireless networks has been broken. Website explaining the crack https://www.krackattacks.com/. Thanks to...
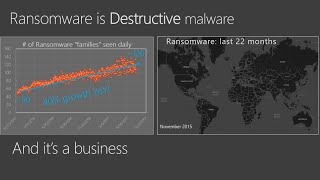

Ransomware, Don't Pay?
Ransomware is on the rise and as long as we pay to get our data back it is a profitable enterprise for cyber criminals. The only...


That's Not the Way Things Work in Government
"That's not the way things work in government." This is the catch all excuse for not doing what needs to be done in the government. The...


Cyber Security News (5 OCT 17)
Cybersecurity and The Law China has is implementing a new Law that requires companies to store all data within China and submit to and...


Cyber-security for Local Governments 2017
In this presentation, given at Maze Live 2017, I cover how the IT control environment overlaps with he financial control environment. ...



















