

TU RMF Roles and Responsibilities (Part 1)
TU RMF Roles and Responsibilities (Part 1) People are a critical factor in any cyber security imitative. In this session we will cover...


Building and Maintaining a Successful RMF Program
TU Building and Maintaining a Successful RMF Program Starting or maintaining an effective and efficient risk management program (RMF)...


Introduction to NIST’s Risk Management Framework (RMF)
TU Introduction to NIST’s Risk Management Framework (RMF) StartFragmentThis introductory session will cover the basic steps of the Risk...

CIS Critical Security Controls v. 6.1
The Critical Security Controls for Effective Cyber Defense has been updated to version 6.1. This new version has a new two-level...

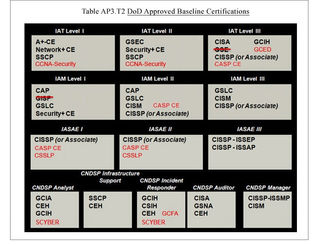
Cyber Security Certifications
People often ask, “What certifications are best in cyber security?” My answer is to follow the numbers. By that I mean do some research...

Free Online Cyber-security Training for Veterans
There is free online cybersecurity training resources for veterans and Active Military members. Federal Virtual Training Environment...

Career Advice in Cybersecurity
This the first edition of the Trainers Underground covers topics of career advice, cyber security certifications, and other topics like...














