
Data Modulation
Here is a video on data modulation. There are two types used in radio waves amplitude modulation AM and frequency modulation FM. Here...


Detecting Insider Threats
Insiders have long been one of the biggest security concerns for organizations. People are known to be the weakest link in the chain of...
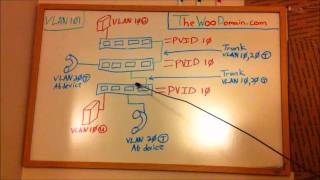

VLAN Basics
Virtual Local Area Networks, or VLANs, are a great way to help you segment network traffic. Often network traffic is segment for...

Routing Tables Explained
Here is a tutorial on how routing tables work. #Network #Network #CNT #CNT52 #Routing


Building a Career as a Systems Admin
If you are interested in employment beyond help desk and would like to work on servers, your best bet is to pursue a systems admin...


Real Life Experience for A+ Cert.
My CNT 51 class, CompTIA A+ certification course, will be assembling 40 computers for Las Positas’ upcoming All Academy Day on April 1. ...


Public Wi-Fi Risks
ThioJoe has a YouTube Channel where he covers a number of tutorials on computers and technology. Here is a good one on the risks of...


Cat 5, 6, & 7, What's the difference?
ThioJoe has a YouTube Channel where he covers a number of tutorials on computers and technology. Here is a good one on different type of...


Dangers of IoT
The Oct. 21st 2016 DDoS attack on the domain name servers of DYN has been the recent topic of many articles lately. The attack left many...


PC Tech Tool Bag
Here is what I normally keep in my tool bag. I should note, I've been IT for about 4 years now. It was only in the last year or so that...














