

New Scams July 2019
Government Imposter Scams We have all received calls or emails purporting to be from some government agency like the social security...


New Scams April 2019
ACH Scam Vendor ACH request fraud is on the rise. The scam works this way, cybercriminals stalk their prey (research or intelligence...


Hacked or Spoofed?
Do you know the difference? You may have seen a friend request on Facebook from someone you know and had thought you were already friends...


Cybersecurity for Local Governments 2018
2018 update on cybersecurity for local governments. This year marks the rise of the new threat to Local Government from nation states...


Most Popular Cyber Scams
Cyber scams and online fraud continue to evolve. Law enforcement and cybersecurity professionals try to prevent online fraud by...


Hacking a Tesla
This is another demonstration of how people can hack into cars. However, just because it is possible does not mean it is practical. Look...


Book Reviews Q1 2018
My recent reading list has included a number of good titles that may in some way relate to cybersecurity. I freely admit that I am in...


12 DEC 2017 Security Update
In this issue will will cover recent news topics in cyber security. #Security #Antimalware #Malware #Hacker #Hacking #Cybercrime...
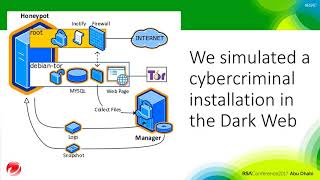

The Dark and Deep
Cybercriminals have a perfect platform for conducting cybercrime. The Dark web is the place where criminals hide, but that is not all...


Where Cybercrime Goes to Hide
Here is a Norton documentary on bulletproof hosting services. Pick where you want to host your data where it is most legally beneficial...
























