

The Wolf
Stop what you are doing and watch this. It's a big ad for HP but you gotta take a minute to view it. Especially after what we were...


Implementation Flaws
Often we find flaws in the implementation of technologies. Once the flaws are found we think companies will work to correct those flaws. ...


Ted Talk - Cybercrime
James Lyne: Everyday cybercrime -- and what you can do about it "How do you pick up a malicious online virus, the kind of malware that...


New Attack Techniques 2017
The Seven Most Dangerous New Attack Techniques, and What's Coming Next "Moderator: Alan Paller, Research Director and Founder, SANS...


What if you Reply to SPAM
This is what happens when you reply to spam email | James Veitch YouTube "Suspicious emails: unclaimed insurance bonds, diamond-encrusted...
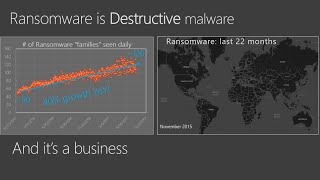

Ransomware, Don't Pay?
Ransomware is on the rise and as long as we pay to get our data back it is a profitable enterprise for cyber criminals. The only...


What should you do about the Equifax data breach?
It is still early in the investigation and new information continues to come to light, but it is clear that almost half of all Americans...


Vigilante Justice
Warning, these videos have profanity. Student Erik Gallagher sent me a link to one of these videos. I found a few more. Here people...


Data Breaches on the Rise
March sees an increase in the number or records from data breaches. At least 17 companies have had breaches and the number of...


iCloud Hostage
Hackers holding 300 million iCloud account details to ransom raise their price to $700,000, despite assurances from Apple What a...
























