

AI in Hacking
Eric Ilmberger CNT 52 Network+ I went looking for news on mass AI attacks but was unable to really find anything. As AI develops further...


Hacking Cars, Plans, and Devices
How safe are we? If planes can be hacked and cars can be hacked, what is preventing terrorists or contract killers from hacking vehicles...


Cyber-espionage Technology Ups the Game
Espionage is nothing new, with the advent of technology why wouldn’t spies take full advantage of the benefits and ease of use technology...


Student Notes November 2017
Don, Since we'd been talking about AI recently in the beginning of class before we get down to the lesson of the day, thought you'd might...


Where Cybercrime Goes to Hide
Here is a Norton documentary on bulletproof hosting services. Pick where you want to host your data where it is most legally beneficial...


The Wolf
Stop what you are doing and watch this. It's a big ad for HP but you gotta take a minute to view it. Especially after what we were...
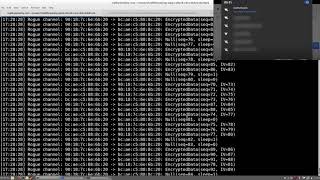

WPA2 Vulnerability
WPA2 Encryption used to secure wireless networks has been broken. Website explaining the crack https://www.krackattacks.com/. Thanks to...


Public Wi-Fi Risks
ThioJoe has a YouTube Channel where he covers a number of tutorials on computers and technology. Here is a good one on the risks of...


Dangers of IoT
The Oct. 21st 2016 DDoS attack on the domain name servers of DYN has been the recent topic of many articles lately. The attack left many...


5 Most Dangerous Hackers Of All Time
Here are 5 of the most dangerous hackers to ever walk the streets of the Internet. #Hack #Hacking #Cybersecurity #Vulnerability...
























