
Policy, Procedure, or Plan
Some standards like PCI and NIST require policies that cover specific topics. Sometimes you will see a requirement for a policy and...

IT Governance & IT Management
Many practitioners use these terms governance and management synonymously. While there is some overlap in practice, there are key...

Cybersecurity Policies Made Easy
People often ask for advice regarding information security or cybersecurity policies. For the remainder of this article, I will use...


Cybersecurity Policy for Local Governments
Here is a sample high-level cybersecurity policy for a city, district, or county. It is designed to be a high-level statement adopted by...

Does Security Awareness Work?
According to the Verizon 2018 Data Breach Report, 93% of data breaches are linked to phishing or social engineering. With stats like...

The Visible Ops Handbook
This is a book review I wrote back in 2007 for a past version of this website. I am resurrecting it because it is still applicable today....
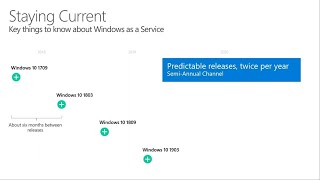

Understanding the Windows as a service
Servicing Windows 10: Understanding the Windows as a service process and improvements YouTube "Windows 10 makes significant changes to...
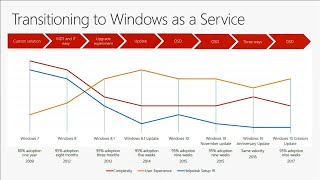

How Microsoft deploys Windows 10 and implements WaaS
It is always interesting to learn how Microsoft uses their own product in an Enterprise environment as large as Microsoft. Lesson can be...


Cyber-security for Local Governments 2017
In this presentation, given at Maze Live 2017, I cover how the IT control environment overlaps with he financial control environment. ...


Create a modern workplace with Microsoft 365
The workplace is transforming - from changing employee expectations, to more diverse and globally distributed teams, to an increasingly...



















