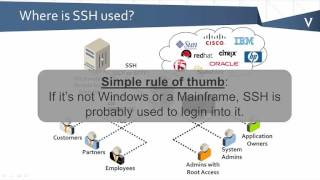

SSH Encryption Analysis
Eric Ilmberger CNT52 Network Fundamentals I did a little more research on symmetrical and asymmetrical encryption because it wasn't...


China is making a Massive switch to IPv6
Eric Ilmberger CNT 52 As China hosts the largest population on the planet, it only makes sense that they would need more IP addresses to...


Extend Wi-Fi Range
For many years people have been using aluminum foil to help enhance and extend the range of their Wi-Fi networks. The question we may...


Spoofing Fully Qualified Domain Names
Spoofing Fully Qualified Domain Names How can you spoof a FQDN? John Hohn covers the history of DNS and name registry to demonstrate a...


Wireshark v. OmniPeak
A common tool for monitoring network traffic that is taught in classes is Wireshark. In part, because it is freely available. However,...
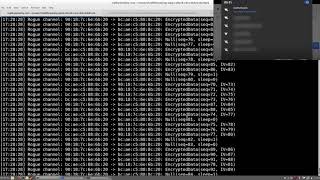

WPA2 Vulnerability
WPA2 Encryption used to secure wireless networks has been broken. Website explaining the crack https://www.krackattacks.com/. Thanks to...


Microsoft Ignite 2017 Keynote
Satya Nadella, CEO Microsoft, oversees all aspects of Microsoft business and leadership--from cloud and mobile development to digital and...


TCP/IP v4 Intro
Introduction to TCP/IP v 4 and Subnet Masking. This is foundational knowledge needed for any computer networking career. Here is a brief...


Visio Admins Best Friend
Visio is a Microsoft Office application that helps users create charts, diagrams, timelines, and illustrations. Most Network or system...
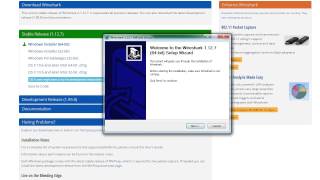

Introduction to Wireshark
Wireshark is a network packet capture and analyzer. It is simple and powerful tool for analyzing network traffic. Here is a series of 8...



















