

Prepare for Ransomware
Recently technical guidance was released for CIOs and CISOs on how to prepare for a ransomware attack. This guide was a joint effort of...


Cybersecurity for Local Governments 2018
2018 update on cybersecurity for local governments. This year marks the rise of the new threat to Local Government from nation states...


Default Security Settings, What Needs to Change?
Today, news agencies and outlets are reporting Information Technology (IT) breaches and loss of protected data at alarming rates. The...


Student Notes November 2017
Don, Since we'd been talking about AI recently in the beginning of class before we get down to the lesson of the day, thought you'd might...


Hacking the iPhone's Face ID
A Vietnamese security firm says it has been able to fool the iPhone X's facial recognition software. In a video released by the company...


The Wolf
Stop what you are doing and watch this. It's a big ad for HP but you gotta take a minute to view it. Especially after what we were...


Spoofing Fully Qualified Domain Names
Spoofing Fully Qualified Domain Names How can you spoof a FQDN? John Hohn covers the history of DNS and name registry to demonstrate a...


The Visible Ops Handbook
This is a book review I wrote back in 2007 for a past version of this website. I am resurrecting it because it is still applicable today....


New Attack Techniques 2017
The Seven Most Dangerous New Attack Techniques, and What's Coming Next "Moderator: Alan Paller, Research Director and Founder, SANS...
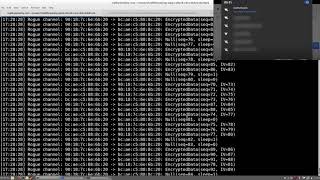

WPA2 Vulnerability
WPA2 Encryption used to secure wireless networks has been broken. Website explaining the crack https://www.krackattacks.com/. Thanks to...
























