
TU Office 365 Secure Score
In this session we cover the Office 365 Secure Score and take a tour of the security and compliance center in Office 365. These tools go...


TU Microsoft's Cloud Compliance Manager
Microsoft newest tool allows Office 365, Dynamics 365, and Azure users track compliance and see what Microsoft has done. Cybersecurity...

Microsoft Compliance Manager
Microsoft has released Compliance Manager for general availability this week. The feature was made available in Public Preview in...


Book Reviews Q1 2018
My recent reading list has included a number of good titles that may in some way relate to cybersecurity. I freely admit that I am in...


College Day RSA Conference
DON’T MISS OUT ON RSAC COLLEGE DAY College students and recent grads are invited to one FREE day of Full Conference access on April 19 ...


We Need Net Neutrality
Net Neutrality is a hot topic now. What does it mean to the average consumer and what does it mean to the future of competition when it...

FruitFly Malware
A Justice Department indictment alleges a 28-year-old hacker from Ohio, created the FruitFly malware and spied on Apple computers for 13...
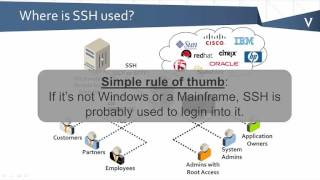

SSH Encryption Analysis
Eric Ilmberger CNT52 Network Fundamentals I did a little more research on symmetrical and asymmetrical encryption because it wasn't...


AI in Hacking
Eric Ilmberger CNT 52 Network+ I went looking for news on mass AI attacks but was unable to really find anything. As AI develops further...


China is making a Massive switch to IPv6
Eric Ilmberger CNT 52 As China hosts the largest population on the planet, it only makes sense that they would need more IP addresses to...














