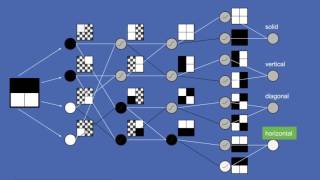

Neural Networks
Neural nets are one-way artificial intelligence work. The question is how do neural nets work? If you are looking into a career...


IT Job Descriptions
This list is a bit dated but gives you a good idea of the job descriptions and tasks different positions might have. Most of these job...


Spoofing Fully Qualified Domain Names
Spoofing Fully Qualified Domain Names How can you spoof a FQDN? John Hohn covers the history of DNS and name registry to demonstrate a...


Bad Rabbit Ransomeware: Get Your Holy Hand Grenade!
On October 24th, ransomware known as Bad Rabbit infected devices primarily in Russia and Ukraine. According to Kaspersky Lab, almost 200...


Passing On Wisdom Career Advice
In this episode of Trainers Underground, Rob, Bryan, and Don talk about career advice that they have been given that really worked for...
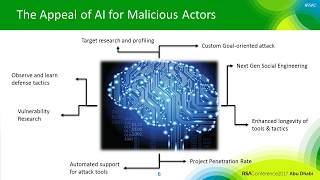

AI in Cyber-security
Here are some views on how AI can help cyber-security efforts. My opinion is we need to adopt AI for cyber-security before hackers learn...

The Visible Ops Handbook
This is a book review I wrote back in 2007 for a past version of this website. I am resurrecting it because it is still applicable today....


Domains of Security
Far from perfect this was my attempt to combine domains of knowledge or common body of knowledge (CBK) to cover all thing in security. I...


Implementation Flaws
Often we find flaws in the implementation of technologies. Once the flaws are found we think companies will work to correct those flaws. ...


Wireshark v. OmniPeak
A common tool for monitoring network traffic that is taught in classes is Wireshark. In part, because it is freely available. However,...














